Hunting the Outlook Zero-Click Exploit
Description:
Your team has been alerted to suspicious activity on the corporate network. An attacker exploited CVE-2023-23397, a critical Microsoft Outlook vulnerability, to silently steal NTLM credentials from an employee’s workstation. The attacker used a malicious calender invite to force an authentication attempt to a rogue SMB server.
Your task is to analyze the PCAP file of this incident. You are required to extract the captured NTLM hash and identify the compromised password, confirm whether is the password part of rockyou.txt wordlist.
- Category: forensic
- Flag format: CTF{plaintext-password-from-NTLM-hash}
Solution:
1. Analyze pcap file with wireshark
There are two information we need to know from the pcap:
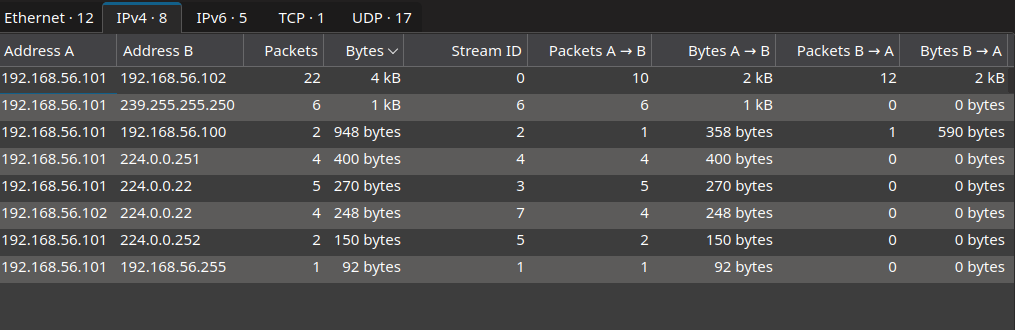
- Identify endpoint of the victim IP address
- Check NTLMSSP protocol with protocol hierarchy
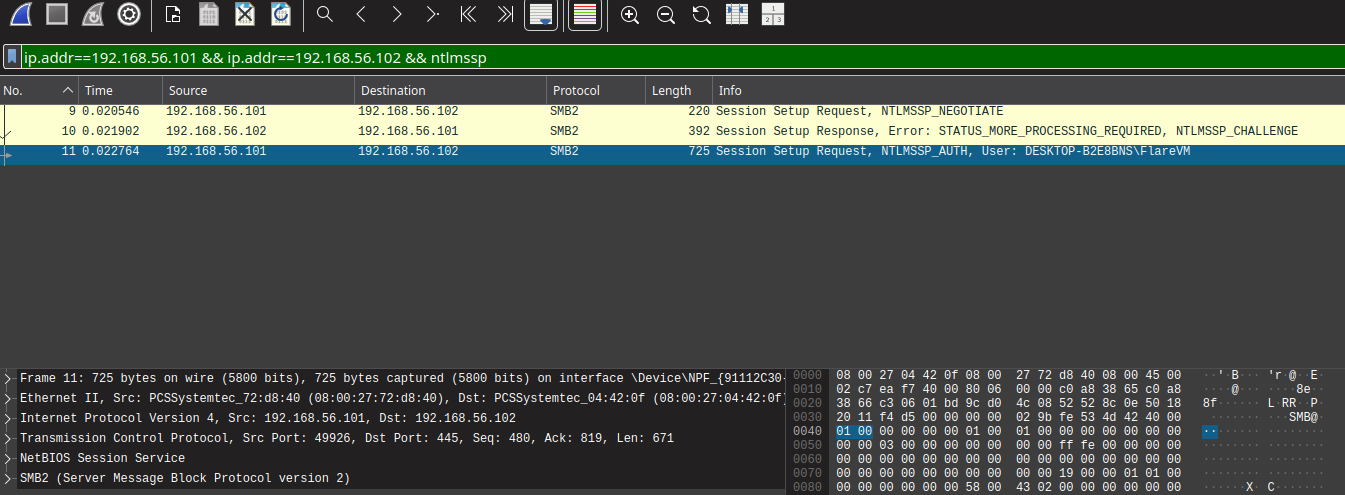
By analyzing the conversation from each endpoint, we can notice two endpoints that transferred 22 packets. Next we use this information as filter along with NTLMSSP protocol. With this Wireshark filter: ip.addr==192.168.56.101 && ip.addr==192.168.56.102 && ntlmssp, we can narrow down and find out the NTLM challenge response packet.
Notice that it shows all three NTLM authentication process (NEGOTIATE, CHALLENGE and AUTHENTICATE) packets.
2. Use NTLMRawUnHide tool to extract NTLM hash
NTLMRawUnHide is a tool to parse pcap and extract NTLMv2 hashes. After running the tools on the pcap, here is the result:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
Searching ../ntlm-leak.pcapng for NTLMv2 hashes...
Found NTLMSSP Message Type 1 : Negotiation
Found NTLMSSP Message Type 2 : Challenge
> Server Challenge : 6ca95c19d3da7e96
Found NTLMSSP Message Type 3 : Authentication
> Domain : DESKTOP-B2E8BNS
> Username : FlareVM
> Workstation : DESKTOP-B2E8BNS
NTLMv2 Hash recovered:
FlareVM::DESKTOP-B2E8BNS:6ca95c19d3da7e96:e1fe4b7c7cdaf8ff9b246a3123c4d1a1:0101000000000000800ce7a2d2b6db01c72ec36ea1a7ac4c00000000020008003700520038004b0001001e00570049004e002d0055003800360044005300370058004d0035003000390004003400570049004e002d0055003800360044005300370058004d003500300039002e003700520038004b002e004c004f00430041004c00030014003700520038004b002e004c004f00430041004c00050014003700520038004b002e004c004f00430041004c0007000800800ce7a2d2b6db0106000400020000000800300030000000000000000000000000300000f9994a49444dc4165f1392f6c3844b71981f2347228f2f3ba63abd0d810343720a001000000000000000000000000000000000000900260063006900660073002f003100390032002e003100360038002e00350036002e003100300032000000000000000000
We have successfully extract the hash, next we can save the hash into a text file so that it can be used to crack with rockyou.txt.
3. Use hashcat or john to crack the hash
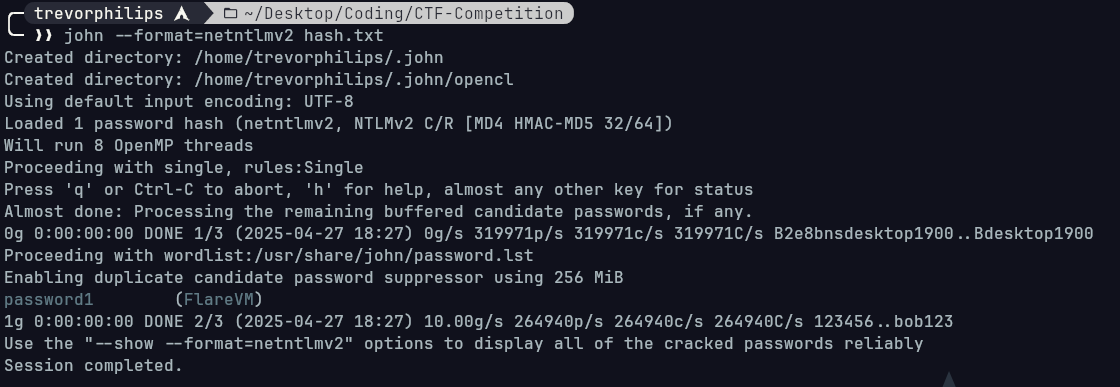 The plaintext password is
The plaintext password is password1.
FLAG: CTF{password1}
About CVE-2023-23397:
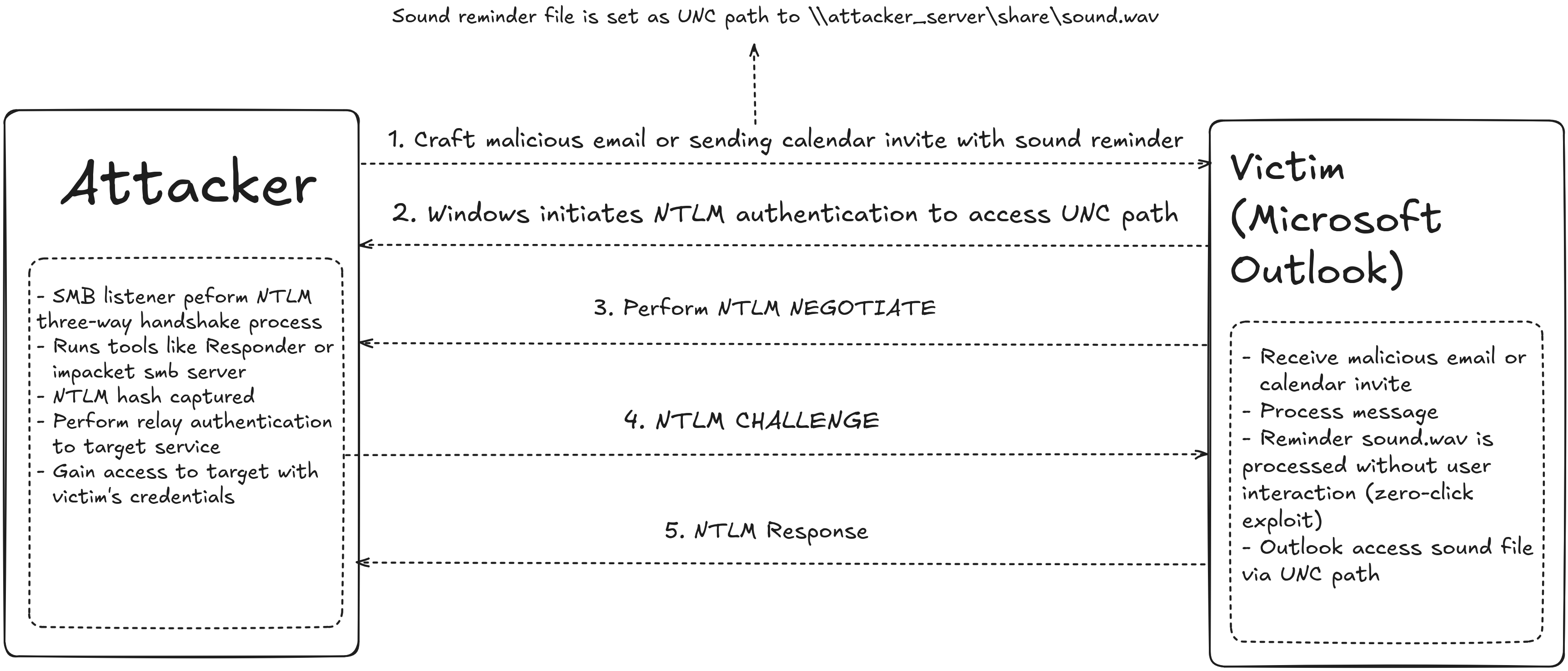
CVE-2023-23397 is a vulnerability in Windows Microsoft Outlook client that exploited by sending a malicious email that able to triggers automatically when Outlook client proceed that email. This exploitation makes it as zero-click exploit as it did not required any user interaction. Below is an attack flow diagram:
The targeted vicitim’s Net-NTLMv2 hashes will be exposed if the vulnerability is exploited. Relay attacks to other NTLMv2 compatible systems might then be carried out using this, enabling the threat actor to pose as the intended user.
When the attacker already has access to the targeted network, relay attacks are far more successful. This is due to the fact that Windows New Technology LAN Manager (NTLM) authentication is typically utilized in Active Directory (AD) environments rather than for Internet-facing services. As a result, remotely relaying compromised hashes ought to be far less frequent.
Refer to this Github repo which explained the PoC in a detailed manner.